Advanced CyberSecurity Services

Managed Bills and Costs

Custom Client Portal

Team to handle Requests
Dedicated Team of G-Net engineers and a Teams channel to communicate.
Highlights
Safe & Cost Effective
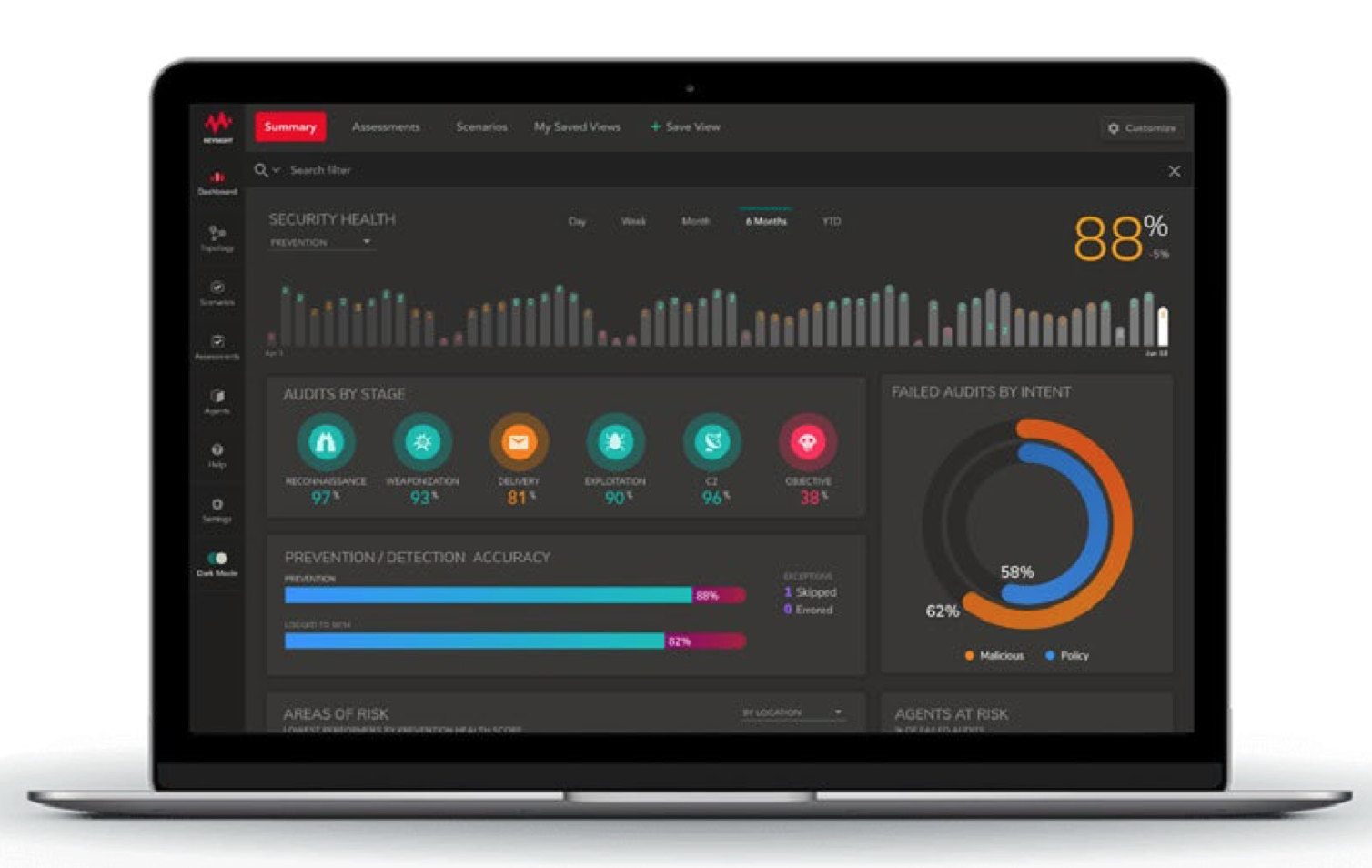
Safe and cost-effective way to measure and validate the effectiveness of your production security tools.
Recommendation Engine
Patented recommendation engine provides clear, actionable insights on how to remediate identifed gaps.
Enhance Security Posture
Enables you to perform automated breach and attack simulations on a regular basis.
Eliminate
Eliminate the assumptions that security controls are deployed and configured correctly.
Pro-active versus Reactive
Complement your IT team with pro-active validation of all phases of the Attack Life Cycle
Time Reduction
Reduce the amount of compliance audit time required with data-driven evidence.
Suite of Reports to include Executive Reporting
Generate on Demand or Scheduled Reports to different IT organization stake holders.
Key Features

Multi-Tenancy
Multi-tenancy access control and segmentation.

Flexible Architecture
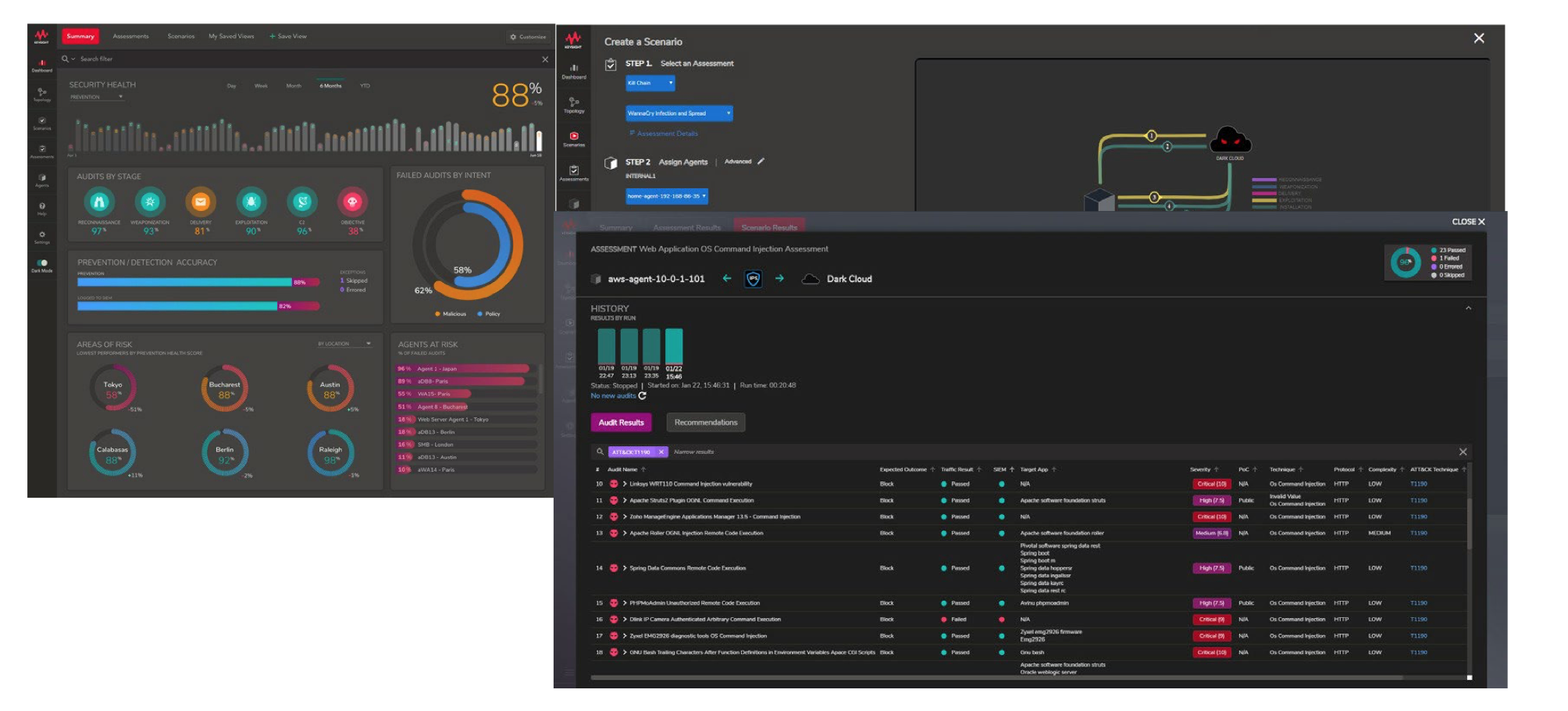
Flexible breach and attack simulation.
.

Actionable Recommedations
Help you improve and optimize security controls
.

Ligthweight Container-based Agents
Enable Operations for on-premises or cloud.

Fully Managed Dark-Cloud
Simulating external adversaries, malicious nodes.
.

Built-in Integration
With top Network Security controls and SIEMs..
Diversified Library of Mitre Attack
Techniques and Threat Vectors.

Out-of-the-Box Attack Libraries
Enables you to simulate Full Attack Chain.

Scheduler Enables
Continuous security assessments.
.
Visual Ladder Diagrams
Complement pre-defined security assessments.

SIEM Proxy Agent
Facilitates communications with SIEM tools.

Agent Tagging
Supports user-provided metadata!
We’re trusted by Businesses across Multiple Verticals





Why Choose Us?
With your over 25 Years of IT experience we’ve seen it all and then some.
Satisfaction Guarantee
At G-Net our core values are the compass we live by to deliver exceptional services and value. Highly trained professionals who actually answer the phone or respond to your email in a timely manner.
A One-Stop Shop
Forget security tool sprawl and alert fatigue. Our BAS platform delivers the highest level of security validation as either a cloud or on-premises platform.
Cloud Simplified
Managing complex cloud infrastructure should not be hard, that’s why there’s G-Net. We make deploying, managing, and scaling your tools to support your cloud applications and infrastructure a simpler process.