Our Services
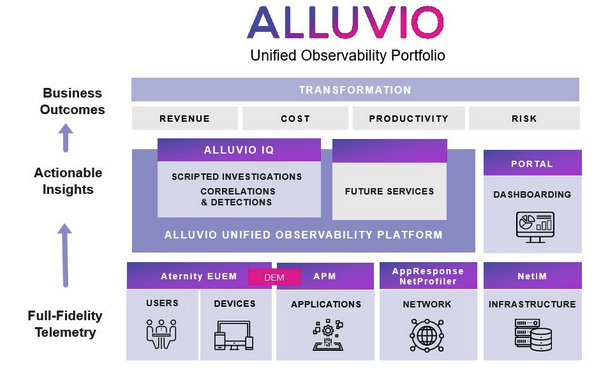
Unified Observability
Apply Intelligence to Problem Detection
Leverage AI/ML to correlate and identify accurate insights that optimize business productivity.
Automate the Investigation Process
Use Automation to handle the scale and complexity of today’s IT environments.
Codify Expert Knowledge
Reduce risk and enable all IT teams to solve more problems without escalations.
Empower Network Operations in WFH
Enable Network Teams to be effective in remote work environments.
Focus on What's Important
Solve problems faster to keep users productive.
Visibility as a Service
Digital Experience Management
Application Performance Management
Network Performance Management
Network Infrastructure Management
Network Flows
Packet Flows
Secure Access Service edge
Unified Cloud Management
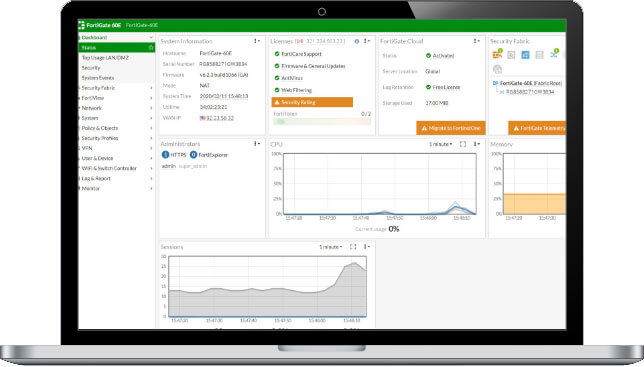
Firewall As A Service
Managed Firewall-as-a-Service (FWaaS)
Service Overview
Managed Firewall-as-a-Service allows G-Net to take over control and management of a customer’s enterprise firewall, to use a cloud-delivered firewall service, and to connect all of the locations the customer has to that firewall and to manage policy centrally. G-Net’s FWaaS is required to enable this service.
FWaaS allows us to secure a customer’s perimeter using cloud-based enterprise-grade next generation security firewall functionality. G-Net’s FWaaS is delivered from G-Net’s robust cloud infrastructure and built on Fortinets’ Next-Generation Firewall technology. The service is automated and orchestrated through our centralized Cloud console allowing configuration, monitoring and management from a single easy-to-understand interface. FWaaS provides one point of policy development and management for multiple offices/locations, and routes traffic through those policy enforcement points as it leaves each office and is destined for other offices, cloud providers, or the public Internet.
Connectivity from the customer location to the G-Net Cloud requires an Fortinet edge device or G-Net approved third party device to create encrypted IPSEC tunnels into the G-Net enterprise-grade security firewall security stack. No separate purchase of any security equipment or licenses is required.
FWaaS functions include
- Network Intrusion Prevention and Detection (IPS/IDS)
- Network Anti-Virus and Anti-Spyware
- Network URL Inspection and Filtering
- Web Application Firewall
- DNS Sinkholing
- Network Encrypted Packet Inspection (SSL Decryption)
- Zero-Day Packet Inspection and Threat Prevention
- G-Net Cloud Edge Connect
- NG Firewall Policy and Configuration Management
- G-Net Cloud console
- Network IP Inspection and Filtering
- Network File Auditing and Blocking
- Network utilization reporting
- Security event reporting
- Secure Cloud Access
- Directory Integration
- Security Log Forwarding
- Internet exposure minimization through direct peering with all major cloud providers (AWS, Azure, Google) & more than 180 content and internet service providers
- Carrier-grade upstream transit capacity in-excess of 150Gbps
FWaaS Reference Architecture
- FWaaS Reference ArchitectureThe FWaaS reference architecture is described in figure 1.0. It depicts a typical customer scenario consisting of headquarters, regional offices, data centers, small office, and mobile users connecting to G-Net cloud regions. Various types of connectivity from customer locations are included such as G-Net Edge Connect appliances and data center connections/cross connects are included. From the G-Net cloud direct connections are made to our ever- increasing number of direct peering partners such as AWS, Google, Office 365, and Microsoft Azure, as well as direct connectivity to the public Internet.
Figure 1 Managed Firewall as a Service
EndPoint Security
EndPoint Compliance
Zero Trust NaaS
Cloud Sand-boxing
SaaS Security
Enterprise Browser Security
Menlo Security
Traditional security approaches are flawed, costly, and overwhelming for security teams. Menlo Security is different. It’s the simplest, most definitive way to secure work—making online threats irrelevant to your users and your business.. More Details
Remote Browser Isolation (RBI)
Traditional security approaches are flawed, costly, and overwhelming for security teams. Menlo Security is different. It’s the simplest, most definitive way to secure work—making online threats irrelevant to your users and your business.
Secure Web Gateway (SWG)
Purpose-built for the cloud, our isolation-powered Secure Web Gateway (SWG) is different. Why? It protects against the evasive web threats that easily bypass all other SWGs.
Cloud Access Security Broker (CASB)
Providing the remote workforce with direct and secure access to SaaS platforms, without interruption. More Details
Data Loss Prevention (DLP)
Providing seamless protection to the most valuable information your business manages.. More Details
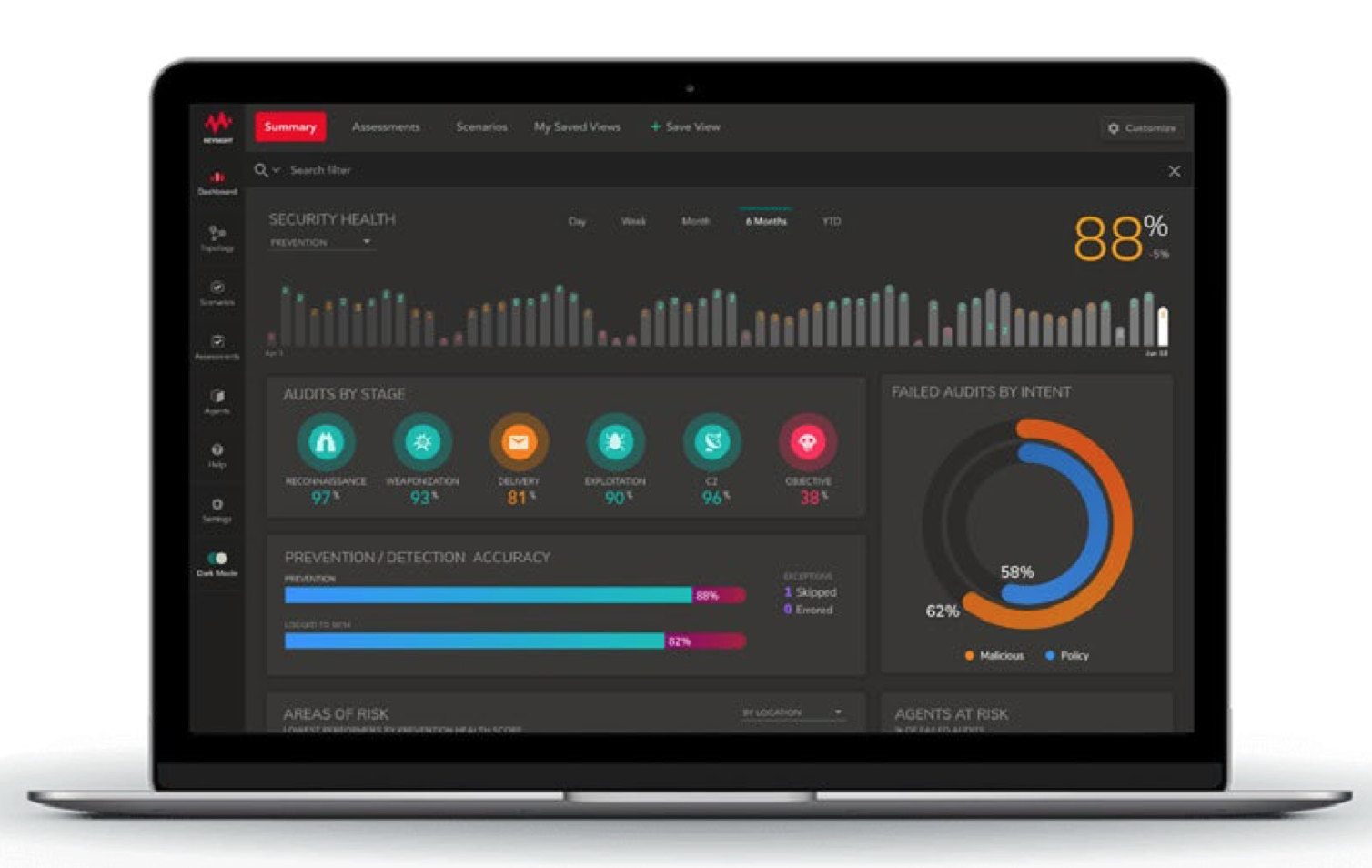
Breach & Attack Simulation (BAS)
Problem: Security is Hard, Misconfigurations are Common, and Breaches are Rampant
Validate your tools, fix vulnerabilities, and prove your network is protected. Part of Keysight’s security operations suite. More Details
Measure
• Measure the efficacy of security posture.
• Identify vulnerable security gaps and misconfigurations.
Optimize
• Prioritize fixes with product-specific remediations.
• Maintain optimal security posture with proactive action.
Monitor
• Assess vulnerabilities on a continuous basis.
• Identify environmental drift before an attack.